Access Control system proftech Kenya
Access Control system, allows you to monitor the movement of everyone who has access to your building, which means you control who can go where and at what time, allowing you to keep access into restricted areas limited to authorized personnel only. It also gives you a log of all movement across access points, providing your security team with valuable evidence in the event of an intrusion into a secure area.
In case you are looking for an incredible way of access control Kenya, then you may need to consider biometric access control.
At proftech, we know how secure biometric systems are and can therefore give you the very best access control systems in Kenya. Due to the delicacy and complexity of such systems, we ensure you that we will install systems that will work, so that you don’t have to keep calling us due to system malfunctions. Note that malfunctions in such complex systems may lead to a lot of unwarranted delays and inconveniences.
Reduce Theft and Accidents
Biometric access control uses unique elements of a human body to identify who to grant access. For example, door access control can be done with the use of a fingerprint scanner. First, the authorized finger prints are scanned and fed into a database. After that, a finger print reader is placed near the door. Anyone who wants entry puts their finger on the reader and only those who are authorized are granted access.
Your Security Needs and Access Control
Our biometric access control systems can be used in different places. You can use them in your home, office or business premises. There are people who even prefer to use them only on the most sensitive areas of their homes or businesses so that they can effectively and powerfully restrict access to those areas. This therefore enhances the security of their valuables and confidentiality of documents and other private items.
We have experienced staff that will ensure they take good care of your installations. They will also answer any queries you may have and give directions as to how best you can use these systems. Call us today to make an order and we will be happy to help.
Most security professionals understand how critical access control is to their organization. But not everyone agrees on how access control should be enforced, Access control requires the enforcement of persistent policies in a dynamic world without traditional borders .Most of us work in hybrid environments where data moves from on-premises servers or the cloud to offices, homes, hotels, cars and coffee shops with open wi-fi hot spots, which can make enforcing access control difficult.
Keep Track of Employees
Access control systems also improve employee productivity by monitoring punctuality and can be integrated with your payroll systems to auto-generate attendance records, which certainly come in handy on pay-day!
In terms of security, access control is an effective long-term, cost-saving strategy for businesses. Clients can request that the system be configured to request for additional credentials (such as a PIN code FRID cards biometrics) before being granted entry, which then negates the need to have all checkpoints manned by guards.
And while keys are easily lost, your biometric fingerprint is intact for life. In the case of proximity cards, it is as easy as deactivating any lost or stolen cards rather than having to replace locks in the case of the traditional lock-and-key solutions.
Access Control is a system designed to allow companies to stay in charge of their security. With selective access, building access systems allow your premises to appear welcoming while offering maximum protection outside threats and from internal challenges such as shrinkage.
Choosing the Best Access Control System for Your Organization
An access control system proactively monitors, manages access and secures multiple of points of entry and exit in real-time, for individuals, vehicles and materials, all from a single location. Door control links to many supporting systems including video and offers full documentation.
Building Access Systems can increase productivity and is particularly suitable for compliance. It may be structured to be automatic or to utilize a controller. It may offer free flow of traffic or require documentation by utilizing a system uses of tamper-proof credentials. They may be physical or digital, using key cards, pin cards or biometric scanners. Access codes via smart phone are also used. Most frequently, key or access cards are used to authenticate identity, especially for apartment security systems. Access Control may be supported by alarms and video surveillance. The more levels involved, the greater the management opportunities.
Door control can simplify flow, reduce costs and liability, manage staff changes and provide ongoing actionable intelligence while reducing security staff. Searchable and stored data reports that are admissible in court, can aid post-incident investigation.
Access Control may also access radio frequency identification (RFID tags) used most typically for supporting wildlife research and protection. The system may be linked to numerous technologies including Identity Management, Visitor Management, Intrusion and alarm panels, Biometrics (fingerprint, retina scan, etc.), Facial Recognition, Elevator Control
Consumers interact with electronic access control systems every day through keyless entry and smart home technology. The first thing that comes to mind is often the remote key, keypad, or key card used to enter an office, car, or home. However, there is a lot more to access control than a FOB and a card reader at the entrance of a door.
The behind the scenes technology determines which electronic access control system is the best application for the area. A commercial-grade access control system provides the initial classification of who gets into the facility and who doesn’t, along with a second level of security, controlling who has access what areas of the establishment down to each file cabinet or drawer containing sensitive information. Sophisticated systems can differentiate access by user, track activity, and provide security logs for administrators. Some systems communicate and coordinate with other security measures for a streamlined and integrated approach to protecting the company, its employees, its assets, and its data.
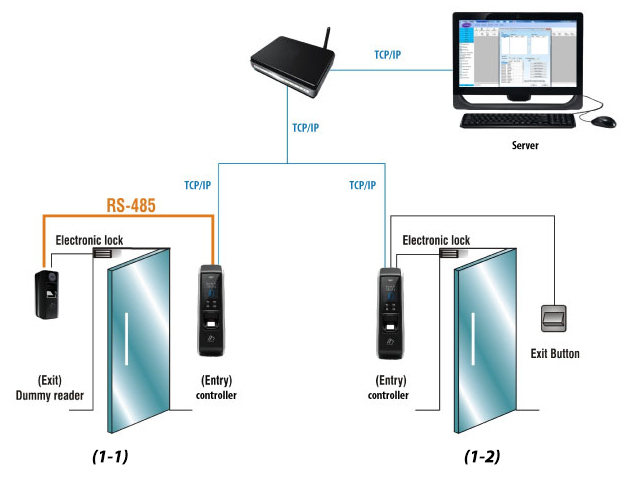
It is recommended to provide Security and Access Control System for Technical rooms, Server Center, Teleco Pops, Electrical rooms and other critical security areas. The Security and Access Control System is consisting of a Server, Workstation, an operating system and application software, and field-installed Controllers.
Controllers are connected to the structured cabling network on a separate VLAN dedicated for security and access control system. The security access system shall have the following Systems and equipment:
- Access Control System: Regulating access through doors, Anti-pass back, Visitor assignment, Time and attendance, Surge and tamper protection, Secondary alarm annunciation, Credential cards and readers, Push-button switches, RS-232 ASCII interface, Monitoring of field-installed devices and Reporting.
- Security System: Time and attendance, and Video and camera control.
Access control provides the machine/human interface between the Security Staff and the Security equipment sub-systems.
Access will comprise intelligent controllers, electronic door hardware and monitoring systems. The system monitors all nominated doors and the control of access through a door by validation of the access cards. The connectivity is provided by a VLAN on the Facility LAN and will be provided by the Telecommunication Contractor. The Access control connect to the server and to other nominated workstations via the provided LAN.
Access control systems extend capabilities, improve operational efficiencies and instill confidence that precious assets, resources and people are secured and protected. HID’s best-in-class access control solutions enable:
- Trusted access, for the right people at the right times
- Safe environments for employees, visitors and contractors
- User convenience and workflow optimization through integrated, mobile solutions
- Increased visibility, with real-time monitoring and cost-control functions
- Investment protection via scalable, forward-looking solutions
- Peace of mind, with expert, personalized concept-to-implementation support
Main objectives of access Control
Enhance the safety and security of the valuable infrastructure and prevent unauthorized entry into the airports.
To identify, categorize, verify and validate personnel data and biometrics credentials in real time.
to minimize human error and opportunities for misuse/encroachment in operational and sensitive areas.
Alert authorities to an attempted intrusion or other irregularities.
Analyze incidents in real time and post event.
Use of advanced technology to minimize human intervention
Access Control system software
- Automatic management and monitoring in real time up to 2,000 terminals
- Time zone function can be set per each terminal and user as a access right
- Password data is encrypted as AES encryption
- Privilege management of manager ID can be granted by using 18 conditions
- All functions (User Management, Group Management, Terminal Management etc..)
- Tracing all transactions on the Server System
Fingerprint Scanners
Fingerprint Scanners is a fingerprint recognition device’s for computer security equipped with the fingerprint recognition module featuring with its superior performance, accuracy, durability based on unique fingerprint biometric technology.
Fingerprint Reader / Scanner is very safe and convenient device for security instead of password, that is vulnerable to fraud and is hard to remember. Use USB Fingerprint Scanner / Reader with our Biometrics software for authentication, identification and verification functions that let your fingerprints act like digital passwords that cannot be lost, forgotten or stolen